Verizon releases Data Breach Digest
Report looks at causes of data breaches, stolen credentials at 42%
02 March, 2016
category: Corporate, Digital ID, Financial, Government
 Victims of data breaches think they are unique, that some hacker or nation state has targeted them specifically and taken them down with a complex, one of a kind hack that will never be seen again.
Victims of data breaches think they are unique, that some hacker or nation state has targeted them specifically and taken them down with a complex, one of a kind hack that will never be seen again.
This isn’t the case.
Over the last three years, just 12 scenarios represent more than 60% of Verizon’s data breaches investigations. Verizon released the inaugural Data Breach Digest that analyzes the cyber breaches that its RISK team has investigated, opening up its case files and giving individuals a view of breaches from the field.
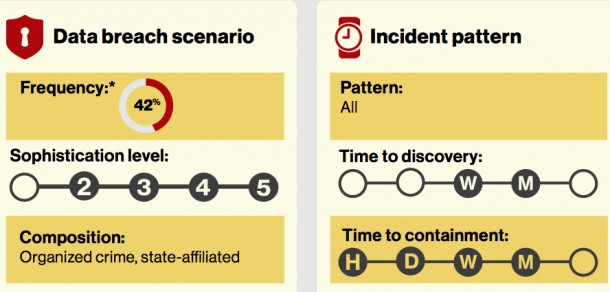
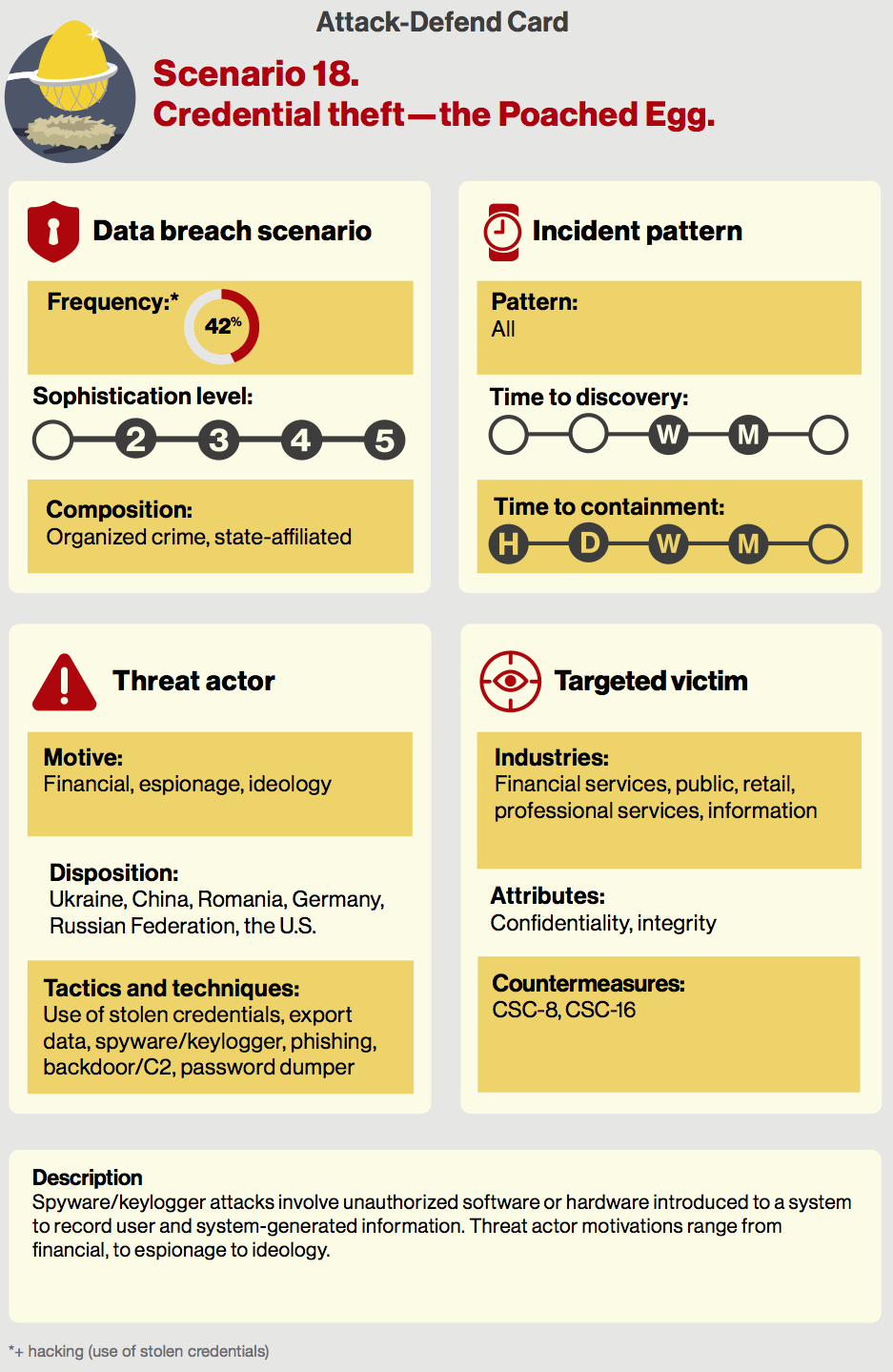
The Data Breach Digest looks at 18 data breach scenarios. These were chosen because of their prevalence and/or their lethality. One scenario detailed is credential theft – which is used in hacks 42% of the time. These hacks can take weeks or months to detect and take just as long to contain.
These breaches involve spyware or keylogger attacks involving unauthorized software or hardware introduced to a system to record user and system-generated information. Hacker’s motivations range from financial, to espionage to ideology.
The Data Breach Digest tells the tale of the RISK team investigating one corporation’s breach. In this case the hacker gained access to a web server and then installed malware capable of dumping passwords and stealing credentials via keylogging.
The hackers compromised several administrator accounts using password dumping, password cracking and keylogging. As forensic analysis continued, Verizon realized that the breadth of credential theft was much larger.
In addition to log data and IP addresses, Verizon recovered a deleted spreadsheet that included a listing of more than 100 usernames and passwords for a specific administrator. This spreadsheet had been exported from a password repository service that the administrator had used to manage personal and professional passwords.
Two-factor authentication wasn’t required to access the password repository service. This set of compromised credentials led to hackers gaining even more credentials and provided them with access to numerous network locations, including several domain controllers.
This ended with a forced password change for the entire enterprise along with removing the malware. A new password policy was also put into place requiring unique password to access each resource. Verizon also recommended two-factor authentication for remote access.
The full Data Breach Digest can be downloaded here.