Understanding RFID Part 7: System Components
05 May, 2008
category: RFID
 By Jerry Banks and David Hanny, co-authors of RFID Applied
By Jerry Banks and David Hanny, co-authors of RFID Applied
RFID implementations are becoming very numerous as they offer an expected benefit over the present way of doing things. Used in the proper situation, RFID can provide a better way of doing business or enable a much more convenient procedure for the consumer or user of a system. In some situations users of software systems may not even know that they are using RFID. Because RFID is being integrated into the way we operate both individually and collectively, there are fewer clear boundaries concerning what constitutes the components of RFID. RF system elements can be as unique as the purpose to which they are being applied. For example, the set of RFID system components that benefit Airbus during its assembly process will be different than the RF data processing needs at Carrefour’s retail operations. This article explores the typical elements that make up RFID components. It also addresses areas where RFID is having a positive impact outside of what are typically considered fundamental RFID components.
As activity occurs in an operation, RF technology senses the situation. Taking action on this RF data at various component levels allows repetitive actions to be completed with greater speed and with added accuracy. Processing real situations automatically opens new doors to cost savings through process improvement. Technology upgrades such as RFID must enable the user to be more effective in a day-to-day job. Almost every business has interest in increasing sales, differentiating its product portfolio in the marketplace, running effective internal operations, and managing customers and suppliers. Recognizing market shifts and consumer buying patterns earlier in the planning cycle will facilitate a more accurate and a closer-to-real-time planning cycle. RFID is an enabling technology for this type of business objective in many instances. To meet such operational objectives, one must understand a general application stack that meets a business need. Figure 1 shows a view from the ground up of many application needs.
Figure 1. RFID Component Application Stack
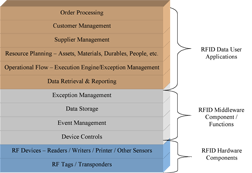
The RFID application stack is broken into three major groups: RFID hardware, RFID middleware, and application software. Each of these groups will use RFID data. The lines of delineation aren’t identical in every usage. However, this general picture is a good starting point for discussion. RFID users will go through a period of discovery as they grow to understand how the technology will impact components in their software system. Depending on each scenario, RF data has the possibility of bringing greater or lesser distinct value to each differing component.
RFID Hardware Components
The most atomic element of RFID is the tag. The communication protocol between the antennas on the tag and on the reader allows the two entities to pass data back and forth. Power may be provided from the reader (passive tags) or from a battery activated tag (active tags) that initiates the communication, as shown in Figure 2.
Figure 2. RFID Connectivity
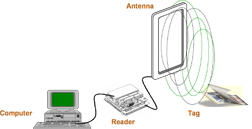
The RF reader will broker the data and manage the physics of the hardware solution set. Typically, reader properties are configurable, giving the reader different operational characteristics in varying environments. The reader normally manages a level of data smoothing, so that near-instant read retries that result from a physical bouncing motion of the tag are minimized. Even though it is usually referred to as a reader, many of these devices also can write or reprogram the tag. Some reader providers offer a controller (or hub) to allow multiple readers to connect through a common port to the middleware.
Middleware Component
RFID equipment must get its information into a data system for usage. Middleware is the link between RFID devices and system software. The needed use of middleware will vary based on the specific implementation. As asynchronous actions occur during a particular scenario, each event must be managed. Middleware has the responsibility to make known when a particular event occurs. Often, related data that is associated with the captured event needs to be assembled and made available to the RFID user for processing. For example, as an RF-tagged box is read, the associated items in the box may need to be reported at the same time for external software to continue processing properly. The pendulum of middleware capabilities swings from a dumb interface where as-is data is simply passed upward, to a complex interface that often has a very specific process logic near the reader. A dumb interface is easy to implement and provides value to fill up data systems with information. The quickest path to customer mandated compliance or data aggregation is a business strategy using a dumb interface. A common disadvantage of these simple message passers is that data may not be effectively weeded out, making data storage near unmanageable in a mid- to high-volume environment. The alternative is a highly intelligent middleware component that makes decisions and filters RFID related information. These more intelligent implementations make complex decisions based on the RFID prior to notifying external software systems. It then provides only the RFID-related information that is necessary for that particular system (filtering out unwanted data). There are pros and cons for each. This sophisticated middleware provides rules such that only selective data is provided to a centralized integrated system.
One of the most successful deployments of middleware exists in semiconductor manufacturing, where the RF device is treated like one of many sensors on process equipment. As transponders are read, the process equipment software conducts a variety of verification steps that consider which item arrived and the changing states and availability of the equipment. Should the set of tagged items be at this process step? Are there other items that are required prior to the tool starting? Additional validation occurs prior to proceeding with the process step. The middleware then makes certain that the proper tool recipe is available to continue processing and commences operation by moving the product through a specific tool. It then provides the RF data with other pertinent attributes to a manufacturing execution system (MES) for storage. One disadvantage of tool specific middleware is that each device or device type will usually have different logic for a specific scenario and operation step. Performing software development and providing support throughout the life cycle for this type of solution is no trivial task in a multifaceted environment.
Storing the data in an organized manner is an important function for an RF implementation. Data storage is necessary for information retrieval at the proper moment in processing. Examples of tag associated data include time stamps, location, a contents list, group ID, last known location, temperature, next destination, and so forth. Such associated persistent data should be kept allowing information to be retrieved at a later time. Three major functional segments are addressed in middleware capabilities: device controls, event management, and tagged object tracking (refer to Figure 1). A detailed discussion of common features and functions are listed in the book RFID Applied.
Open-Loop Components
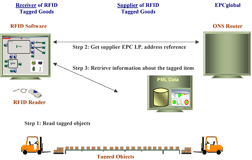
Today, enterprises have a growing need for developing a supply chain management strategy. EPCglobal has introduced an open-loop architecture that has support from some of the world’s most influential organizations and companies. These efforts are intended to assist in supply chain initiatives. The EPCglobal vision that is shown in Figure 3 illustrates that suppliers of goods will host a data warehouse with information about the products they provide to their customers. This data warehouse is accessed across the internet where data is stored in a format called the Physical Markup Language (PML). This is a derivative of the XML format. Received tagged objects are individually identified using RFID readers by their customers. Once identified, the customer may connect to an Object Name Service (ONS), which acts like a router and will direct the customer to the internet address of the data. The ONS is similar to the Domain Name Service that is used to look up an IP address for Web sites. Data related to the tagged object is then available across the internet. This provides an ability to operate in an open loop fashion. When a tag is read, the receiver can retrieve current data about the tagged object from the supplier. The supplier can regularly update the information related to the data as necessary. For example, the RFID tagged product may have an expiration date, some knowledge of specific properties of the contents shipped or other information that is necessary for the receiver of the product to understand.
Figure 3: EPCglobal Vision for Open Loop Data
Extended Business Components
Data unused is opportunity lost in the business world. Meaningless data can be a burden to an operation. This is also true with RFID activity and stored events. RFID is an enabling technology that can allow business software components to operate at a greater degree of efficiency. System’s such as an MES or enterprise resource planning (ERP) can benefit greatly from RFID. The next article in this series, Part 8, examines an example scenario of RFID used in these extended business environments. As RFID components become integrated into other business applications, they have the opportunity to contribute to the added value of the operation. Like many technologies, there is yet much to be discovered with how to exploit RFID data.
Summary
RFID components and their extended set of business components will vary from user to user. A guiding business vision is important to develop as RFID technology becomes understood and deployed. Integrating RFID into business processes and reevaluating these processes is important to achieve maximum benefit from RFID. Tying RFID data to existing software components and then taking action on the situation can provide added value and benefit to an enterprise.
This is the seventh article in a series that explains the principles of RFID. It was created for RFIDNews by Jerry Banks, Tecnológico de Monterrey, Monterrey, Mexico and David Hanny, Applied Materials, Salt Lake City, Utah. The authors are two of four co-authors of RFID Applied, John Wiley, 2007, ISBN-10 0471793655; ISBN-13 978-041793656.




