U.S. Federal agencies lagging with PIV, strong authentication
04 March, 2015
category: Digital ID, Government, Smart Cards
 More than half of cyber intrusions to U.S. federal agencies could have been prevented using strong authentication, according to a report from the White House Office of Management and Budget. The annual report to Congress on the Federal Information Security Act (FISMA) details how agencies are still behind when it comes to using PIV credentials and strong authentication technologies.
More than half of cyber intrusions to U.S. federal agencies could have been prevented using strong authentication, according to a report from the White House Office of Management and Budget. The annual report to Congress on the Federal Information Security Act (FISMA) details how agencies are still behind when it comes to using PIV credentials and strong authentication technologies.
In Fiscal Year 2014, which ended in September, US-CERT found that 52% of cyber incidents were related to or could have been prevented by strong authentication implementations. This is an improvement over the previous Fiscal Year that was at 65%. Strong authentication for civilian agency user accounts is at only 41%, below the 75% target.
E-Gov Cyber reviewed agency performance against authentication-related FISMA Metrics. As part of the reporting process, agencies describe the different authentication methods employees use to gain access to Federal information and networks.
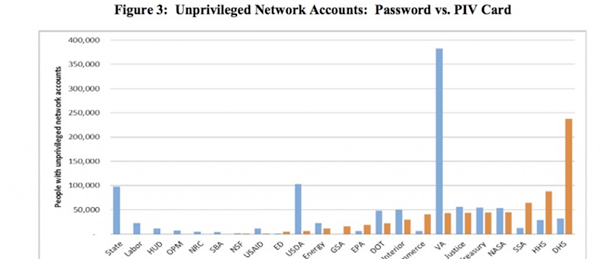
Some 16 agencies have weak authentication profiles, enabling the majority of unprivileged users to log on with user ID and password alone. This makes unauthorized network access more likely as passwords are much easier to steal through either malicious software or social engineering. The Department of Veteran’s Affairs has more than 350,000 users accessing information with user names and passwords and the State Department has 100,000.
The Department of Homeland Security leads the way for PIV access with almost 250,000 employees using the credentials followed by Health and Human Services with almost 100,000. The Defense Department was not included in this survey but also requires its employees to use the Common Access Card for strong authentication.
While the substantial number of unprivileged user accounts — of which there are more than 5.3 million — are able to log on to Federal networks with only a user ID and password more troubling concerning, is the number of privileged network accounts that are able to log on with only a user ID and password. Unprivileged user accounts are the ones most employees use to access email and different work applications and services. Privileged accounts are the administrators of those systems and able to create new accounts and access additional information.
Privileged user accounts, of which there are 134,287 across the government, possess elevated levels of access to or control of Federal systems and information, increasing the risk to resources if their credentials are compromised. There are 18 agencies do not require a majority of their privileged network users to log on using two-factor PIV authentication. Health and Human Services and the State Department are the worst offenders when it comes to having privileged users accessing networks with user names and passwords.