The importance of a registration authority
02 June, 2011
category: Corporate, Digital ID, Government
 Why an ID store needs to be the first investment, best practice lessons from FIPS 201
Why an ID store needs to be the first investment, best practice lessons from FIPS 201
FIPS 201, PIV and the Draft FIPS 201-2 often get thought of as a standard defining the technology associated with strong authentication, digital signing and encryption using digital certificates and public key infrastructure.
While the standard and the underlying special publications do define the credential technology components an equally important part of the specification addresses best practices for establishing an identity and enrollment suitability.
The first phase in the FIPS 201 process of establishing an identity that can provide high assurance and interoperability is a crucial aspect of the standard where PIV and PIV-I Interoperability (PIV-I) establish best practice and warrant focus by identity professionals. This identity creation process needs to be a template for any trusted identity.
Much of what is written about PIV and PIV-I gets caught up in PKI. But just as much, if not more, attention needs to be paid to why organizations need to create an enterprise identity service and the architecture to support this. Fundamentally there needs to be a single authoritative source for identity data also known as a registration authority. This needs to be the case even if organizations have opted for identity as a service and outsourced their PKI.
One of the best results from the Federal Identity, Credential and Access Management (ICAM) initiative is the separation of the lifecycle management of each of the ICAM components. In order to progress in the ICAM maturity model organizations must start with an enterprise service to support the identity creation function and as a result support the creation of a registration authority.
A registration authority can serve as a powerful focal point to implement policy for the creation of a range of credentials. This can range anywhere from high assurance multi-step, multi-role, multi-person registration to doing self assertion via a simple Web registration portal.
One of the important things that come from starting with the creation of a registration authority is the ability to create an identity vault that properly safeguards data. The other significant benefit is that it invokes an architecture that properly restricts the frequency of access to data that by its very nature is long lived and does not need to be updated.
In fact the ICAM process has an underlying logic that comes from the inverse relationship to the frequency with which data needs to be accessed and its life cycle. Identity data is long lived and seldom needs to be accessed – but still needs to have a chain of trust maintained – while certification related attributes have shorter life cycles and are more frequently accessed. The following inverted triangle can be used to represent these relationships.
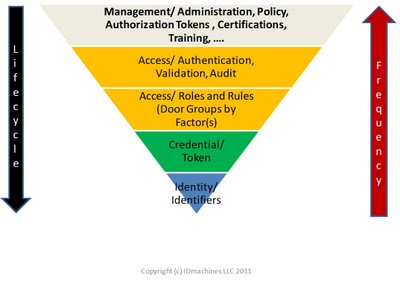
The enterprise registration authority and the associated identity vault sit at the bottom of the triangle. It is the building block on top of which enterprises will implement ICAM. It provides the foundation for enterprise governance, risk management and compliance by providing a common identity footing across these regimes and activity.
ICAM needs to be done in order; identity then credentials, then access, then management of other attributes and certifications. In order to take the first step in getting the “I” in place a registration authority needs to be put in place and organizations need to look to PIV and PIV-I and the process they define.
When doing these organizations need to make sure they put in place a process that meets the highest level of assurance they will need to meet. Supporting lower levels of identities is easy to do from a high assurance identity infrastructure. Supporting higher levels of identity is extremely difficult if not impossible with a low level of assurance identity infrastructure.
The need to get things right at the start and to support the full range of use cases is all the more reason to adopt PIV and PIV-I as enterprise policy for identity creation and to establish this as policy and a requirement for the enterprise registration authority.
There is a long standing lesson from manufacturing that building quality in to a process is much more cost effective than trying to add it on after the fact. In building 21st century identities quality – high assurance – needs to be built in at the beginning. Getting identity – as opposed to simple identifiers – right necessarily needs to have a registration authority and the associated roles and policy that can meet the requirements as laid out in FIPS 201 and supported by the PIV and PIV-I frameworks.
In doing so organizations not only maximize the use cases they can support but also maximize the return on their identity infrastructure investment.