ID 1.0 and 2.0 have failed, time for ID 3.0 or ID Next Gen
21 June, 2012
category: Digital ID, Government, Library, Smart Cards
By Jeff Nigriny, CertiPath
Identity in our online world is well understood to be broken. Broad recognition of this began 18-years ago with a cartoon depicting dogs using the Internet pretending to be people. When was the last time a news cycle didn’t include a story about stolen identities or the failure of passwords as a security mechanism?
The U.S. Federal Government launched the National Strategy for Trusted Identities in Cyberspace in an attempt to “correct a market failure.” All of the components exist for online identity to be successful, and now it’s time to reassemble it.
As a gross simplification, ID 1.0 was the advent of user ID and password-based mechanisms that bound an individual to a service provider’s specific application or network domain. ID 1.0 went wrong in some very specific, avoidable ways. Low-assurance identities serving low-value transactions have proved to be ineffective.
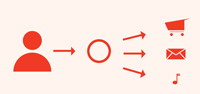
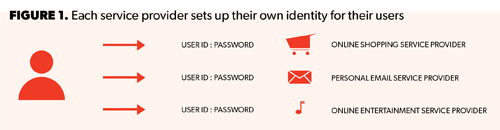
Each service provider has its own identity mechanism. This one-to-one identity to service provider ratio has driven users to select the same identity credentials–user IDs and passwords–for all providers on all applications and sites. Low-assurance identities coupled with the same credential in use at all places empower attackers and undermine confidence in the entire concept of online identity (See Figure 1).
ID 2.0 attempted to make identity credentials portable and/or higher assurance, but solutions such as one-time passwords suffered from a lack of orchestrated roll out between service providers and identity providers.
By design, Internet services did not consider security or identity federation as operational requirements. The concept of portable identities between service providers was not considered at the outset. Each service provider was responsible for the full process of onboarding new users, establishing identity, giving them a credential and managing of the identities over time.
If we fail to recognize the reasons this occurred, Identity Next Generation will be no more successful.
For ID 1.0/2.0, online identity was predominantly a technology challenge. Today, however, the technical challenges enabling identity portability have largely been solved. We are now faced with crippling policy and governance issues caused by an immature ecosystem that was shaped through commercial pressures alone.
Online identity needs to be about a secure, fraud resistant form of identity first and a convenient transaction enabler second. Emerging federation solutions within ID 2.0 have been largely positioned as a single sign-on mechanism across popular social networking sites, extending these site providers’ missions beyond social networking into the role of an identity provider. Identity providers and service providers have taken the path of least technical resistance at every turn. The security and fraud issues inherent in these low-tech, low-assurance authentication schemes continue to make it easy for the attackers perpetrating identity theft (See Figure 2).

In ID 2.0, online identity and the attributes used to extend it are difficult to manage and protect. Once an individual elects to use a social media site as an identity provider–for example Facebook–the default behavior is to share everything about the individual with the service provider’s application. This far exceeds the mandate of an identity provider, yet it is the very phenomenon that has led to Facebook’s significant market share as an identity provider. Specifically, an individual’s profile data is a marketing bonanza for service providers so these web and e-commerce sites love Facebook Connect. Identity providers and service providers alike have commoditized identity data taking advantage of the fact that its use is currently under regulated.
ID 3.0 or ID Next Gen
The next generation of online identity doesn’t need to be a complete redo. In fact some of the identity mechanisms and models available today are fundamentally correct. Consider how service providers link a user ID and password with a text message code to improve authentication for access to services. For example, Google+ requires 2-factor authentication for access and many financial institutions require more than one factor of security to use online banking (See Figure 3).
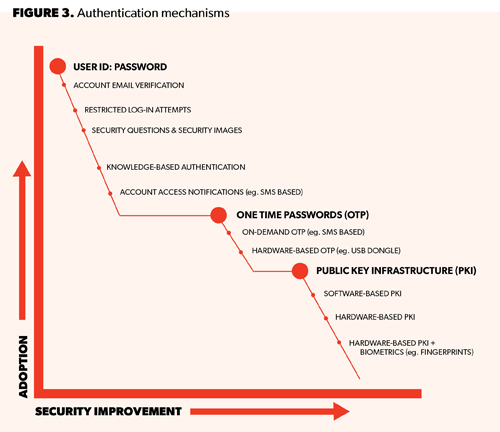
The market failure that necessitated the national strategy is broadly a chicken and egg problem. Leveraging a new identity mechanism requires both the identity provider as well as the service provider to simultaneously adopt the new technology, but each needs the other to justify a mass rollout.
Problems with strong credentials
High-assurance identity usage has suffered from other roadblocks as well. Service providers have not centralized on a single credential type, leaving the credential service providers fractured and regionalized. When someone wanted to buy a credential, they found the physical locations to obtain one to be few and far between. However, this is rapidly changing with the advent of the PIV-I smart card based public key identity credentials.
As we migrate to ID Next Gen, there are new concepts and definitions that support the ecosystem. To facilitate discussion about what’s next, we use the following definitions:
- End-entity–an individual with associated attributes
- Attribute–a quality or characteristic inherent in or ascribed to an end-entity
- Claim–an assertion by an Identity Provider about an end-entity and its associated attributes
- Vetting–the process of inspection and adjudication of claims
- Identity–an association between vetted claims and a subject, certified by a trusted authority
- Credential–a physical or logical representation of an identity issued by an authority
- Credential Service Provider–an organization that issues credentials to the end-entity enabling the end-entity to authenticate themselves within the federation
- Identity Provider–the organization in the federation that authenticates the end-entity for a given transaction and provides a claim to the service provider about that end-entity. Different identity federation models may vary by push and pull style mechanisms.
- Community of Interest–a set of likeminded service providers
- Federation Operator–an organization that provides the governance of the federation for a Community of Interest. The operator defines the rules for an authentication event and states what attributes can be passed from an ID provider through the federation operators to a service provider.
- Service provider–an organization that provides a service to an end-entity
These present a fairly complex ecosystem for ID Next Gen. But with these definitions in mind, it’s not difficult to show comparative issues between ID 1.0/2.0 and the next generation. The most critical difference is the separation of the community of interest, the ID provider and the service provider.
The credential service provider issues the long-lived credential to the end-entity. Fundamentally, the end-entity uses their credential for authentication to the ID provider who then presents the necessary claim for access to the service provider’s applications.
There are key properties ID Next Gen must exhibit to overcome the barriers that thwarted ID 1.0/2.0:
An identity is only useful in the context of a Community of Interest. The profile of an appropriate claim, including the policies that define the vetting of attributes for a given population, need to be defined by a community of interest. The federation operator provides governance over these profiles for the community, ensuring enhanced security and smooth migration over time. Additional granularity of policy can be achieved through the overlay of assurance levels.
An ID provider will not be authoritative for all attributes in the scope of an identity claim. Identity providers and attribute providers will have to support RSS-style feeds so that changes in identification can be received. For example, if an employee receives additional certification or access right, this would be able to be updated through this feed. This will support both front end and back end attribute exchanges, the former that is automatically pushed and the latter that can be requested if needed.
ID Next Gen extends the scope of form factors an identity may take. It must enable the end-entity to authenticate to the ID provider with their strongest identity credential and receive a derived credential at a lower level of assurance matching the form factor of the service provider they wish to access.
ID Next Gen must continue to support user convenience without sacrificing security. Consider three core properties that we feel are required within the ID Next Gen ecosystem:
- One-click login
- Easy two- and three-factor support
- Single-sign-up to any service provider’s application
ID1.0/2.0 illustrated the importance of building user convenience into a security mechanism, despite the paradox it creates. One-click login–implemented as a common graphic used across service providers in any community of interest–must be standardized as a default part of the identity ecosystem.
Identity assurance will continue to be an important concept but can be vastly simplified for the end user. ID Next Gen must enable users to register their mobile device with their ID provider and standardize easy two- and thee-factor authentication services, and then to have an easy two-factor OTP service that a provider can invoke when two-factor authentication is required. Similarly biometrics, while not as common for online identity applications, could be addressed as an add-on service and authenticated between the user’s PC and the ID provider.
Finally, Single sign-up is a usability enhancement benefiting not only the end user but also the service providers and ultimately the identity providers. Currently provisioning new accounts is manually intensive and error prone for service providers. This is especially true for service providers in the financial sector supporting “Know Your Customer” rules that need high quality claims for identities and attributes.
Privacy must be designed into ID Next Gen to inspire trust. Enabling users to understand how their identity information is proliferating in the system is a key capability for use of ID Next Gen. While many mechanisms exist to accomplish this, ID Next Gen must incorporate an auditing/reporting element. Much like credit monitoring tools that alert one to activity involving their credit record, this system must implement identity and attribute usage reporting. When a service provider uses an identity or further queries secondary Identity providers for additional attributes, it must report this usage back to the primary ID provider. The ID provider must share this information with users in an easy to query service.
Federation Operators will provide identity directories for Communities of Interest. These will not be master records of all known people but rather a convenient means to link Identity providers, community service providers and others within the federation. All participants in a given federation must know where to acquire identity data that has been verified, corroborated and hosted by an ID provider. The ID provider will facilitate secure access to this data and will advertise metadata to make it more useful. For an ID Next Gen directory to be useful within a specific community of interest, it must store the following: those identity providers certified to assert identities, secondary Identity providers/attribute providers known to have information about end-entities for which a primary ID provider is authoritative, the home realm of the credential service provider for a given end-entity to facilitate subsequent attribute queries from a service provider, and a trust store list of signing certificate authorities that issued the assertion signing certificates in use at each of the identity providers.
ID Next Gen must support legal discovery between parties in the federation. The legal responsibilities of the involved parties must be spelled out, and each participant must be able to support the other in dispute resolution. There must be mechanisms to demonstrate the end entity’s transactional intent to the satisfaction of the service provider. The common dispute “I didn’t buy that nor did I receive it” must have a simple resolution. It must be straightforward for an ID provider to show which credentials and attributes were put together to deliver a claim to the service provider for authorization of a purchase. It also must meet the requirements of legal scrutiny.
ID 2.0 has shown us the basis of an Internet economy opportunity. There is room for improvement to enhance the user experience and trustworthiness of a networked society using the properties identified for ID Next Gen. These enhancements are not anticipated to be free, as they are not least-common-denominator based solutions.
An economic model between parties must be developed to support the enhanced capabilities in a federated solution that can provide the ease of one-click login, EZ-2 and EZ-3 factor authentication, along with the backing of legal force. Credit card and cellular markets have demonstrated that such issues can be solved. Moving forward, the Internet can no longer afford to be the source of identity theft made easy. ID Next Gen is overdue.
Top 10 properties for ID Next Gen
- Prevent identity theft and subsequent loss of control over one’s personal information. The user must have a way of seeing who is using their identity data to provide confidence in the solutions offered by ID Next Gen.
- Enable third-party corroboration of identity attributes.
- Be easy to use, consistent in operation and supported ubiquitously.
- Be viewed as cool to use.
- Facilitate user choice so they can select the identity data they are comfortable sharing and require service providers to notify the user as to what is mandatory to access their service.
- Enable portability of identity between identity providers, similar to the ability to move your mobile number across carriers.
- Build protections to safeguard users from nefarious individuals trying to behave as them online. ID Next Gen must operate within a legal framework that provides non-repudiation and a predictable distribution of liability across all participants in an identity system. This could be similar to the fraud system credit card issuer have in place.
- Avoid “mega records,” to eliminate fear of creating a national identity system.
- Attach to a vibrant ecosystem, for example, LinkedIn, Facebook, PayPal, Salesforce.com, and medical applications.
- Straddle the old and the new. If you consider the identity to be a form of key and the application trying to authenticate a user to be the lock, ID Next Gen must assist in the migration towards more secure forms of locks.