Exploring the ‘Magic Quadrant’ for authentication
19 May, 2014
category: Corporate, Digital ID, Financial, Library
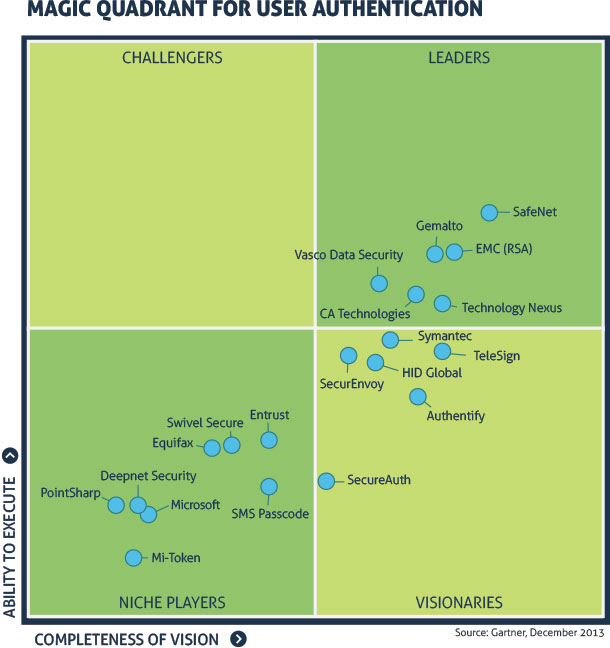
Safenet, Gemalto, EMC, CA Technologies, Vasco Data Security and Technology Nexus are Gartner’s choices for top user authentication technology companies in its recent “Magic Quadrant for User Authentication” report.
Their main conclusions: Perhaps 50 vendors of the 200 or so in the market have credible offerings, and the top six above account for most of the market by customer and end-user numbers.
Succeeding, Gartner says, means moving with the market to mobile and cloud solutions and realizing that the legacy approaches are fast becoming obsolete.
The consultancy rated 20 competitors according to their “ability to execute.” To Gartner, that means the “quality and efficacy of the processes, systems, methods or procedures that enable their performance to be competitive, efficient and effective – and to positively impact revenue, retention and reputation.”
Gartner also rates companies according to their “Completeness of Vision,” or as they put it: “their ability to convincingly articulate logical statements about current and future market direction, innovation, customer needs and competitive forces.”
Gartner’s famed “magic quadrant” places companies in one of four quadrants defined by execution along the y axis and completeness of vision” on the x.
Companies that are competent but behind others are placed in the lower-left hand “niche player” box. Those that have vision but lack execution are placed to the lower right “visionary” quadrant. Companies that can execute but lack vision land in the “challengers” box, and companies that have it all – the top six, in this case – end up in the top right-hand corner, or the “leaders” quadrant.
The report groups user authentication technologies into key categories including:
- Lexical knowledge-based authentication (KBA): A combination of password and answers to questions the user knows
- Graphical KBA: A pattern-based method that asks the user to produce a pattern of cells or in some cases a set of images or categories of images for each login
- X.509 token: Similar to other tokens but often in the form of software or smart cards with the venerable X.509 public key infrastructure.
- Out of Band authentication: This category of methods uses an out-of-band channel – for example, SMS or voice telephony – to send a password to the user that must be entered
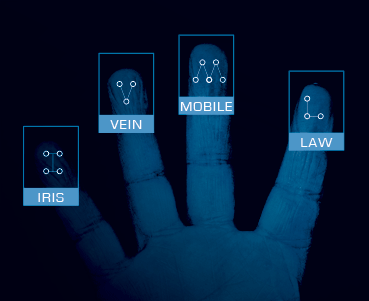
- Biological biometrics: Characteristics such as face, iris, veins in the hand or fingerprints, usually together with PINs or passwords
- Behavioral biometrics: Voice, typing rhythms, a predetermined hand movement, etc.
- Contextual authentication: Other information about the user such as whereabouts, a specific endpoint, etc.