2016 worst passwords announced, suggests user education is failing
18 January, 2017
category: Corporate, Digital ID, Financial, Government, Health
The results are in and the worst password for 2016 is … drumroll please … “123456.” Again.
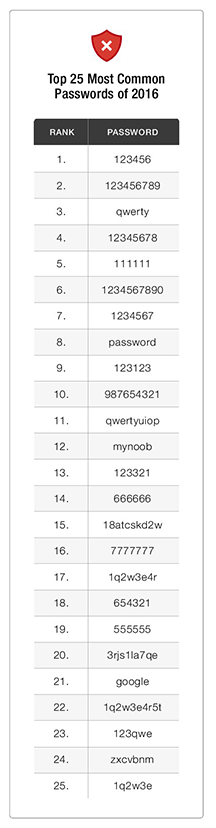
For this study, password management solution provider Keeper analyzed more than 10 million passwords that were made public in 2016 breaches. From this database, they determined the 25 most common passwords. The results look very much like recent years with sequential numbers, adjoining keyboard characters and common words securing individual’s digital lives.
Since little has changed, I will not re’hash’ — no pun intended — the call for unique, long, randomly generated passwords. Instead lets explore the new ideas that spring from this analysis. It highlights three important challenges, each earning its own share of the blame for the continued problems.
 First, education about the need to strengthen passwords is now old hat, yet still we see the following sad state of affairs:
First, education about the need to strengthen passwords is now old hat, yet still we see the following sad state of affairs:
• 17 percent of users are safeguarding their accounts with “123456”
• four of the top 10 passwords – and seven of the top 15 – passwords are six characters or less
This suggests that end user education is falling short.
If you buy this argument, it leaves us with two choices: revamp the education process or assume that some portion of the end user base will not be educated and thus will remain at risk until passwords are replaced.
Second, the results highlight a problem with site owners. Too many are apparently still enabling weak passwords if the user opts to employ them. By this time, one would hope that all site owners were putting at least basic protections in place.
Finally, another interesting point is that two totally random passwords – “18atcskd2w” and “3rjs1la7qe” – appear in the top 25 list. Because these passwords are fairly complex, this would only occur if the same user was setting up tens of thousands of accounts and reusing the password.
But why would this happen?
Likely it is the result of bots setting up fraudulent accounts with email providers so that the user can promulgate spam, phishing or other attacks via auto-generated dummy accounts.
Authors of the Keeper study conclude that, “email providers don’t appear to be working all that hard to prevent the use of their services for spam … and they could do everyone a favor by flagging this kind of repetition and reporting the guilty parties.”
So, as we enter 2017, the problems that continue to plague self-selected passwords are coming from all levels.
Despite years of education, a significant number of users still opt for weak passwords. Though breaches are public and damaging, many site owners still haven’t mandated strong passwords or better yet required multi-factor authentication. And finally, though we know that fake email accounts used for spam and phishing are key sources of compromise, some public email providers are not taking the basic steps to limit fraudulent account creation.
Sounds a lot like 2007 rather than 2017.