IoT: A new frontier for identity
12 January, 2015
category: Corporate, Digital ID, Financial, Government
 Steve Hanna, Senior Principal Technical Marketing, Chip Card & Security segment, Infineon Technologies
Steve Hanna, Senior Principal Technical Marketing, Chip Card & Security segment, Infineon Technologies
Cyberspace and real life are merging. With the Internet of Things (IoT), individuals and devices are increasingly connected to the Internet and physical objects are seamlessly integrated into information networks. Machines and robots are able to sense and analyze data, enabling control of the physical world from a distance. The IoT will change the way we live, work and communicate. No business will be unaffected in the long term. But these big changes imply new challenges, particularly with respect to security.
Security is essential for IoT, especially with respect to identity. If we’re going to connect our houses, cars and factories to the Internet, they must be secured. Individuals, machines and devices must be securely identified so that only authorized access is permitted. Private user data and corporate secrets must be protected from theft and fraud. And all of this must be easy to use – not compromising user experience. Therefore, security should be designed into IoT systems from the beginning, not tacked on later.
The Importance of Security Hardware for IoT
Stuxnet, BlackEnergy, and numerous other recent attacks have shown that IoT systems cannot be adequately protected with software alone. Security software is easily bypassed by clever attackers, who can then remotely control physical systems. The combination of software and hardware offers an optimal balance between security and flexibility. Security chips provide protection even if software is compromised.
User Ide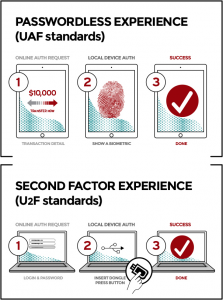 ntity for IoT
ntity for IoT
IoT users demand remote access to their devices from anywhere, but still need ease of use and strong security. Username and password authentication fails to meet these requirements since passwords are painful to enter and easily stolen. Recently, the FIDO Alliance released standards for an open, scalable, interoperable set of multi-factor authentication mechanisms.
IoT users benefit from FIDO in two ways. First, they get stronger security. Second, the complexity of managing device credentials is vastly reduced. As illustrated in Figure 1, FIDO permits users to associate their online accounts with a local hardware security token. Then they can use this token to authenticate and other systems, either with or without a PIN.
Device identity for IoT
With the rise of IoT, device security and especially identity is more important than ever. IoT devices control critical systems such as cars, factory systems, door locks, and security cameras. Yet they are exposed to a variety of network-based threats. To block unauthorized parties and provide security, IoT devices must be able to conduct mutual authentication with users, other devices, and the cloud. Fortunately, device identity technologies are well established and widely available.
Cryptographic authentication is the best approach to IoT device identity. IoT devices are fully capable of establishing, maintaining, and employing long cryptographic keys. There is no reason to employ passwords for device identity. With security hardware, these cryptographic keys can be protected against disclosure.
Some security chips – such as the open standard Trusted Platform Module (TPM) – go further than establishing device identity by also performing encryption and detecting device compromise. Monitoring system integrity is especially important for IoT because a rogue device with proper credentials can cause real physical damage.
Identity for the industrial internet
The Industrial Internet is the application of IoT concepts and technologies to industrial purposes. For example, next-generation manufacturing uses networking to integrate the entire supply chain from supplier and customer, enabling suppliers to customize production to match demand. In such an environment, identity must be verified and communications must be protected end-to-end to make sure that customer demand is properly met. Therefore, all elements of the system from customer to supplier must be secured.
To improve system security and integrity, security controllers can be integrated in all parts of an Industrial Internet system from a tablet used by customers ordering products to the factory line where the products are manufactured and beyond into shipping, distribution, wholesale, and retail. These security chips can establish product, device, and user identity, perform encryption and authentication, and maintain device integrity. Furthermore, these security solutions offer protection of sensitive IP and process knowhow.
Conclusion
In the Internet of Things, strong identity for users and devices is required. Without strong identity, attackers can cross the cyber-physical boundary. Such attacks are taking place now. Because of the many applications of IoT technology, the impact of these attacks is not restricted to the smart home or connected car, but extends to industrial automation, health care, and many other domains.
Fortunately, standards and technologies for strong identity are available without sacrificing ease of use. Hardware security is required to limit the impact of software vulnerabilities, which are ever present. When designing IoT systems and other systems that link cyberspace and the physical world, strong identity implemented with secure hardware should be a requirement. Only in this manner can safety be protected.
About the AVISIAN Publishing Expert Panel
At the close of each year, AVISIAN Publishing’s editorial team selects a group of key leaders from various sectors of the market to serve as Expert Panelists. Individuals are asked to share their unique insight into different aspects of the campus card market. During the months of December and January, these panelist’s predictions are published at SecureIDNews.




