Toopher enables two-factor ‘invisible authentication’
20 May, 2014
category: Corporate, Digital ID, Financial
 Toopher is touting invisible authentication but also may have one of the coolest tag lines for an identity company out there: “cool enough for James Bond and your mom can use it too.”
Toopher is touting invisible authentication but also may have one of the coolest tag lines for an identity company out there: “cool enough for James Bond and your mom can use it too.”
Once an enterprise enables a site for Toopher, a user’s mobile device can serve as a second factor of authentication, says Roman, Gonzalez, marketing director at the company.
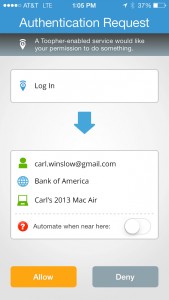
A consumer logs in to a Toopher-enabled site and opts to enroll their mobile device. They are asked to download the Toopher app to their mobile, if they have not already done so.
A message is sent to the app, detailing the site to be added to the user’s Toopher chain. The consumer can choose to allow or deny the site. After approving the login request the individual would be logged on to the site.
After this enrollment has been completed, the invisible authentication takes over. Toopher uses the geolocation feature of the mobile device, learning where a user typically logs in to various sites. If a login comes from a location that is not typical, a request is sent to the mobile to further authenticate prior to allowing the transaction.
The system can also be used to authorize only specific transactions from a provider’s suite of services, Gonzalez explains. For example, if an individual is transferring funds or doing another high-risk transaction, Toopher can be used to authenticate the identity.
The idea is to make transactions more secure without having to pull out the mobile device for every login, Gonzalez says. “It’s an invisible user experience,” he adds.
Toopher is focusing on the financial services market for account access and also has a product that enables consumer to validate payment card transactions. The company also has products available for employee and enterprise access control.



